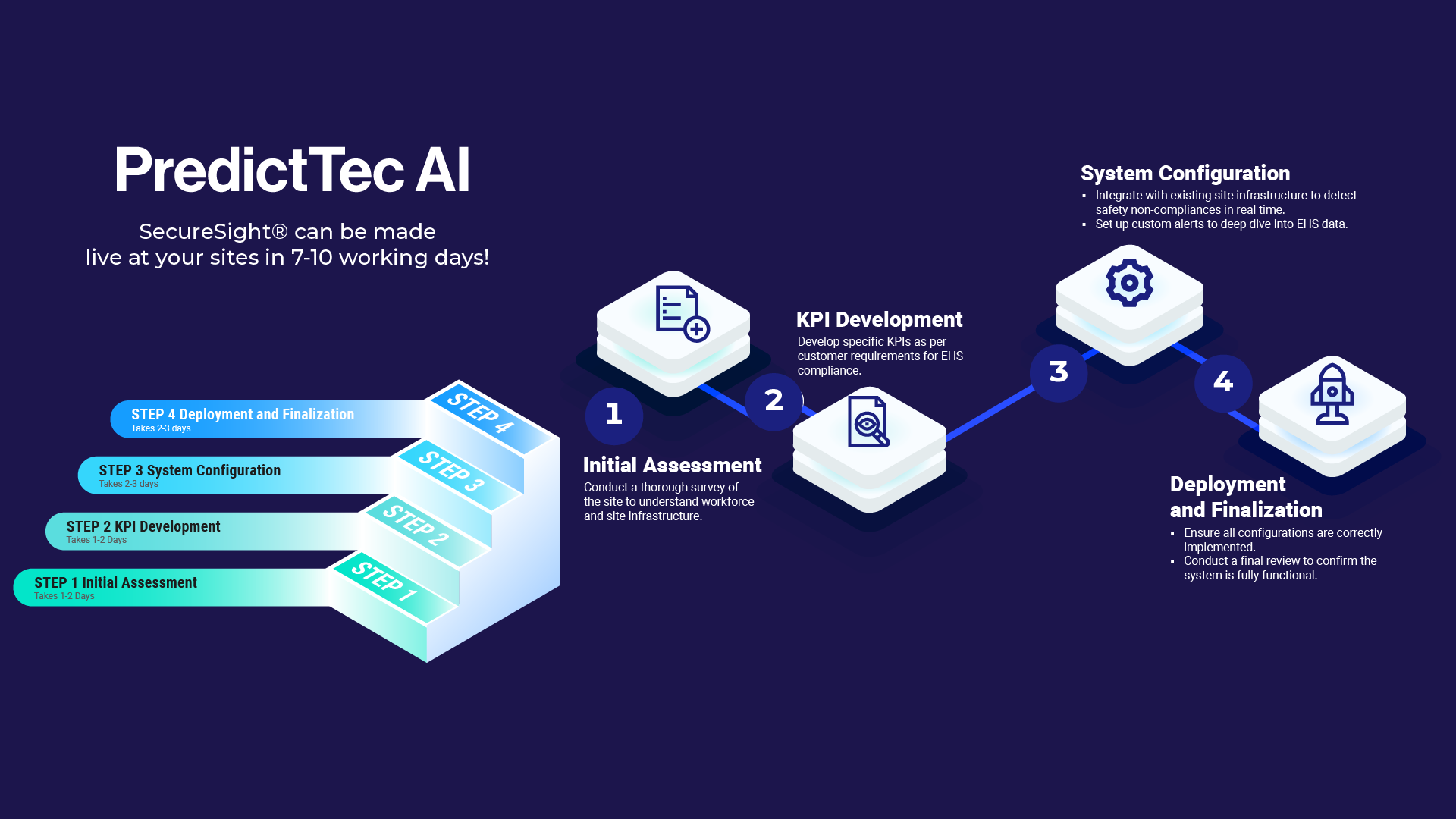
Implementing SecureSight: A Comprehensive 7-10 Day Timeline for Enhancing Your Security
Deploying a cutting-edge security solution like SecureSight is a critical step toward safeguarding your organization’s workforce, assets, and data. While the process can vary depending on your existing infrastructure and specific organizational requirements, SecureSight can typically be implemented efficiently within 7 to 10 working days. This blog post walks you through a detailed, step-by-step timeline to set clear expectations and guide you through the deployment journey.
Why a Structured Implementation Timeline Matters
Implementing a security system is not just about installing software or hardware; it’s about integrating a solution deeply aligned with your site’s unique operations and compliance needs. A clear, phased timeline ensures minimal disruption, maximum customization, and effective risk mitigation, setting your organization up for long-term success.
Step 1: Assessment and Planning (Days 1-3)
The foundation of a successful SecureSight deployment begins with a comprehensive assessment and well-thought-out planning process.
Site Survey and Workforce Analysis:
Experts conduct an on-site survey to gain a full understanding of the physical environment and workforce dynamics. This survey examines site layout, personnel traffic, and operational workflows to identify critical security points.Developing Specific KPIs:
Based on the survey findings, specific Key Performance Indicators (KPIs) are developed to meet the customer’s requirements, ensuring SecureSight aligns with organizational standards and internal protocols.Implementation Plan Creation:
Combining survey insights and KPIs, a detailed project plan is crafted. The plan highlights integration points with existing systems, any necessary customizations, milestones, and expected outcomes.
By the end of this phase, your organization will have a clear roadmap, a deep understanding of how SecureSight will fit within your infrastructure, and identified objectives for deployment.
Step 2: Integration and Configuration (Days 4-10)
The next phase focuses on turning plans into action—seamlessly integrating and configuring SecureSight within your environment.
System Integration:
SecureSight is connected to your existing site infrastructure and relevant data streams. Whether this involves interfacing with access control systems, CCTV networks, or workforce management platforms, smooth integration is key to effective operation.Customization and Configuration:
The system settings are tailored to address your organization’s specific security needs. This includes setting alert thresholds, defining access controls, and programming automated compliance checks aligned with your KPIs.Testing and Validation:
Before finalizing deployment, rigorous testing is conducted to ensure all components operate harmoniously. This step verifies that SecureSight not only meets but exceeds security and compliance expectations.
Outcomes After Implementation
Upon completing this implementation timeline, your organization will have a fully operational SecureSight solution customized to your unique environment. Key benefits include:
Enhanced Security Posture:
Proactive monitoring and rapid threat detection minimize risks.Tailored Insights and Reporting:
Data-driven visibility into workforce and site activities supports informed decision-making.
Final Thoughts
Implementing SecureSight efficiently requires careful coordination, customization, and testing—but the benefits are well worth the effort. By following this 7-10 day timeline, your organization can confidently deploy a security system that not only protects but empowers your workforce and operations.
If your team is ready to advance your security infrastructure with SecureSight, a structured approach like this ensures a smooth transition and maximized value.